
In today’s hyper-connected world, productivity apps are like digital Swiss Army knives, they help us plan meetings, manage tasks, take notes, and organize our digital lives. But with convenience comes risk. A new and alarming trend is emerging: spyware apps disguised as productivity tools.
These stealthy threats are not just targeting tech novices; even experienced users can fall victim. Understanding how these deceptive apps operate and how to defend against them is crucial. Trusted solutions like Mobicip are stepping up to empower users with advanced protection in this rapidly evolving digital landscape.
Understanding Spyware Apps
Spyware apps are designed with one sinister purpose: to secretly monitor and steal user data without consent. Whether it’s personal conversations, banking information, or location data, spyware operates covertly, often without raising the slightest suspicion.
According to the Cybersecurity and Infrastructure Security Agency (CISA), “Spyware is among the most insidious forms of malware because it silently operates in the background, gathering sensitive information and relaying it to malicious actors.”
How do spyware apps work?
Spyware apps are engineered to appear benign. Once installed, they hide their true intentions behind a friendly user interface while collecting:
- Browsing histories
- Text messages
- Login credentials
- Location tracking data
- Camera and microphone recordings
Over time, spyware has become increasingly sophisticated, using encryption and code obfuscation to avoid detection by traditional antivirus programs. The line between legitimate productivity tools and malicious spyware has become alarmingly thin.
The Appeal of Productivity Tools
Why productivity apps?
Because they are trusted, essential, and commonly used. Apps for calendars, note-taking, file management, and project collaboration form the backbone of personal and professional life.

From Medium
A report by App Annie revealed that productivity apps are among the most downloaded categories globally, with usage increasing by 125% during the pandemic.
Productivity apps are a goldmine for hackers because:
- They require extensive permissions: Access to storage, contacts, microphones, and even location services.
- They blend seamlessly into daily use: Who would suspect a to-do list or file organizer?
- They are indispensable: Users are less likely to uninstall a productivity app they depend on.
As cybersecurity analyst Sarah Brown said,
“When users trust an app with their workflow, they often lower their guard, which is a vulnerability that cybercriminals exploit ruthlessly.”
Techniques Used by Spyware Apps
Spyware developers employ a variety of deceptive techniques to stay under the radar. Here’s how:
Mimicking Popular Apps
Spyware often masquerades as clones of popular apps. For example, a fake “Google Calendar Pro” app might use identical icons and user interfaces, making it hard to spot the difference at first glance.
Excessive Permission Requests
An innocuous-looking note app might request access to your call logs, text messages, or even your camera. Always ask yourself: Does this app truly need these permissions?
Evading Antivirus Software
Modern spyware uses encryption and polymorphic malware techniques to change its code signature, evading detection by standard security software.
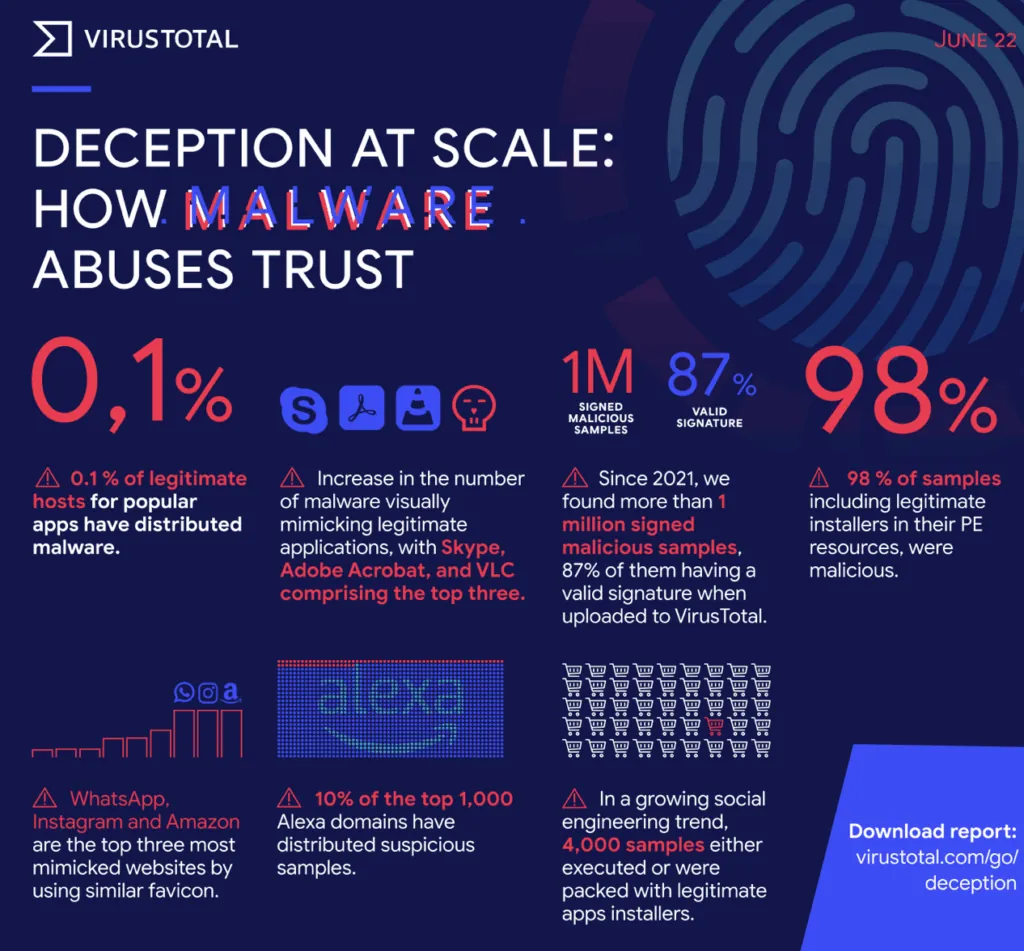
From Virustotal
Fake Interfaces and Hidden Functions
Some spyware apps present a basic user interface to satisfy the user while running powerful spyware functionalities hidden in the background. For instance, a file manager app may have a working but simplistic UI, while in reality, it’s silently uploading your files to a remote server.
As cybersecurity expert Daniel Miessler warns,
“The most dangerous malware doesn’t crash your system; it convinces you it’s your friend.”
Impact of Spyware Apps on Users
The damage caused by spyware apps extends beyond simple privacy violations.
Privacy Violations
Spyware apps collect highly sensitive data:
- Private emails and messages
- Bank account numbers
- Health records
Once collected, this information is often sold on dark web marketplaces or used in targeted cyberattacks.
Financial and Emotional Consequences
The financial implications can be severe. Identity theft, fraudulent transactions, and blackmail are common consequences. Emotionally, victims experience anxiety, loss of trust, and the trauma of personal violations.
Broader Implications
On a societal level, spyware undermines trust in digital infrastructure. As users grow wary of legitimate apps, innovation and adoption of new technologies slow.
“Trust is the currency of the digital economy. Spyware apps threaten to bankrupt it,” says Dr. Michelle Green, a cybersecurity researcher at Stanford University.
Real-World Examples of Spyware Apps
The problem isn’t hypothetical. Here are real cases:
- “X- File Manager”: A seemingly harmless Android file manager app was discovered to be transmitting users’ personal data to servers in another country.
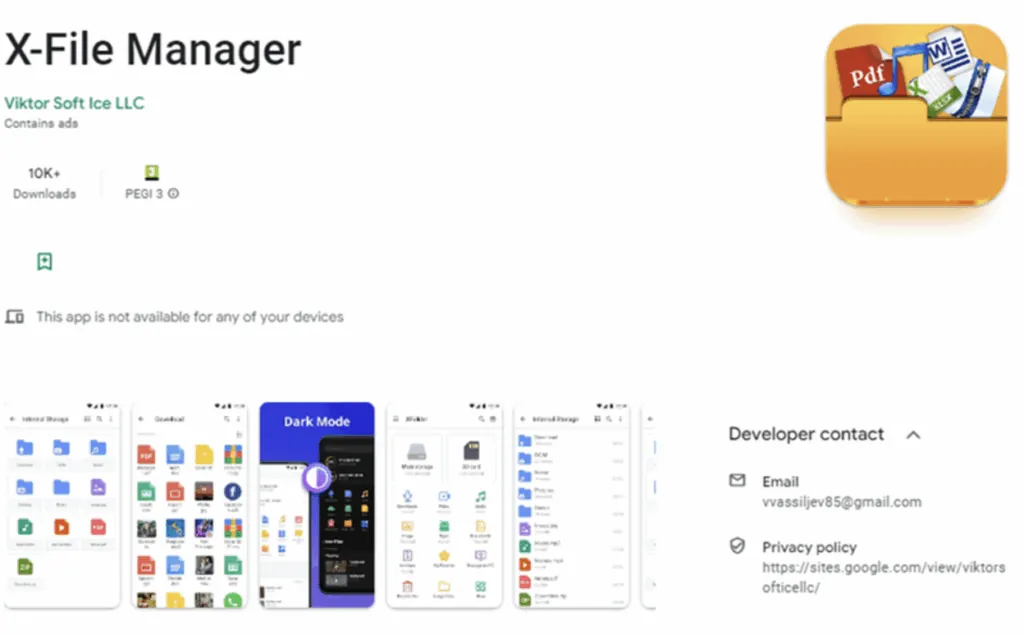
From bgr
- “Quick Notes”: This popular note-taking app was secretly recording audio clips without users’ knowledge.
- “Calendar Pro+”: Disguised as an advanced scheduling tool, it embedded spyware that tracked user movements and call records.
Check Point Research recently documented over 250 apps posing as legitimate productivity tools, yet secretly loaded with malware and spyware functionalities.
How to Identify Spyware Apps
Although spyware is evolving, users can still take proactive steps to spot potential threats:
1. Review App Permissions
Be critical of what an app requests. A calendar app shouldn’t need access to your microphone.
2. Monitor Battery and Data Usage
Spyware often operates in the background, consuming excessive resources.
3. Verify Developers
Research the app developer. Lack of an online presence, vague company names, or limited information are major red flags.
4. Use a Trusted Security Tool
Apps like Mobicip provide real-time monitoring and automatic alerts when suspicious apps are installed.
Preventive Measures
When it comes to spyware, prevention beats cure. Here’s a comprehensive list of best practices:
Use Reliable Security Software
Solutions like Mobicip offer more than just basic antivirus. Mobicip provides:
- Content Filtering across apps and websites
- Real-time Location Tracking
- Customizable App Control
- Screen Time Management to minimize exposure to risky platforms
Download Apps from Trusted Sources
Only download apps from Google Play Store, Apple App Store, or official websites. Even then, read reviews critically.
Educate Yourself and Your Family about Spyware
Awareness is the first line of defense. Teaching children and less tech-savvy family members about digital hygiene is essential.
Keep Your Devices Updated
Software updates often patch security vulnerabilities that spyware apps exploit.
Regularly Audit Installed Apps
Perform periodic checks on all devices. Remove unfamiliar or unused apps promptly.
How Mobicip can Help
Mobicip is more than just a parental control app. It’s a comprehensive cybersecurity tool for families and individuals concerned about digital threats.
Key Features of Mobicip that can Protect Against Dubious Spyware apps
- App Blocking: Block suspicious or inappropriate apps easily.
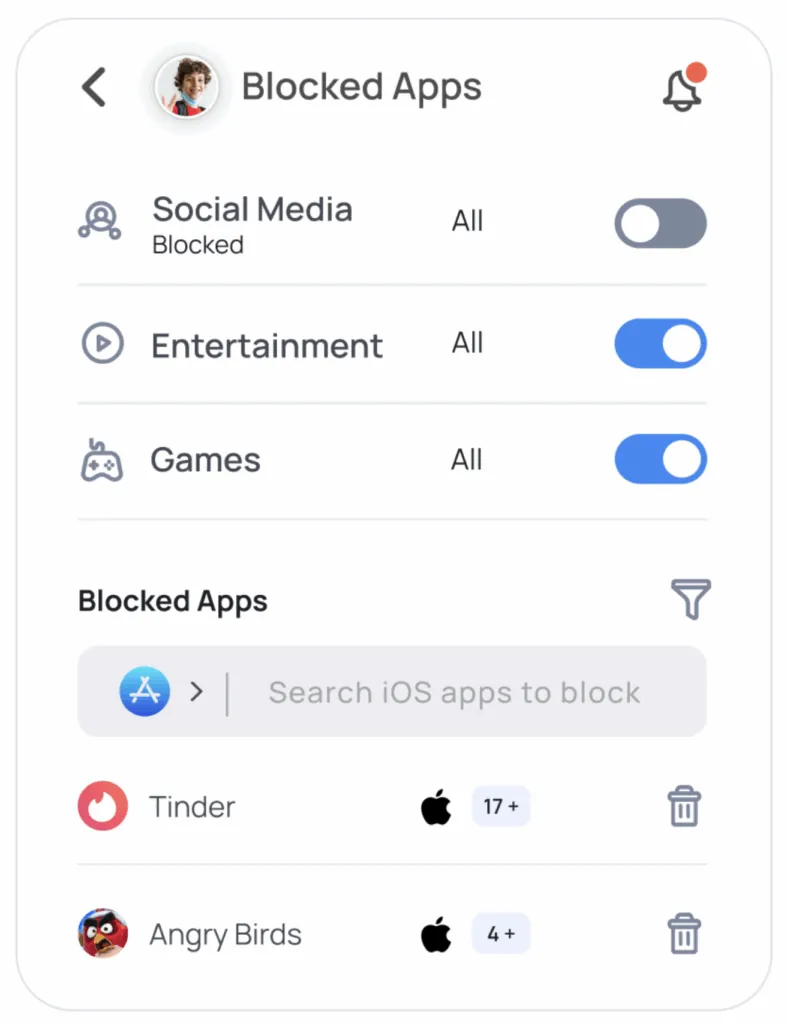
- Activity Reports: Get detailed daily activity reports.
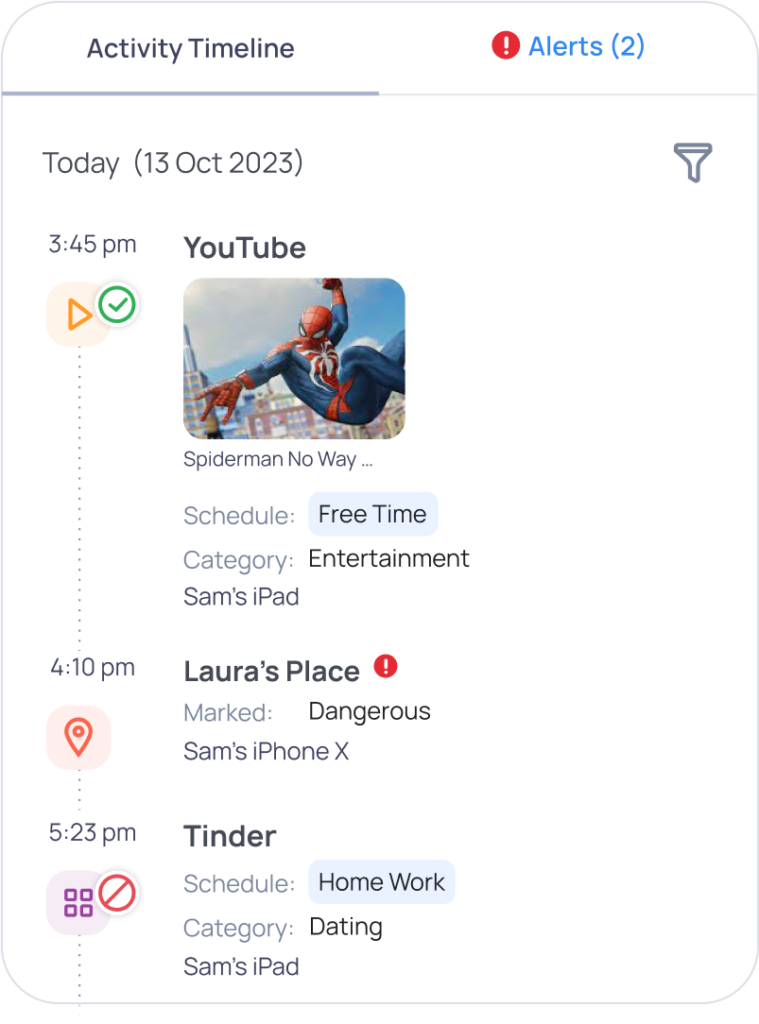
- Real-Time Monitoring: Monitor and set alerts for internet activity across devices
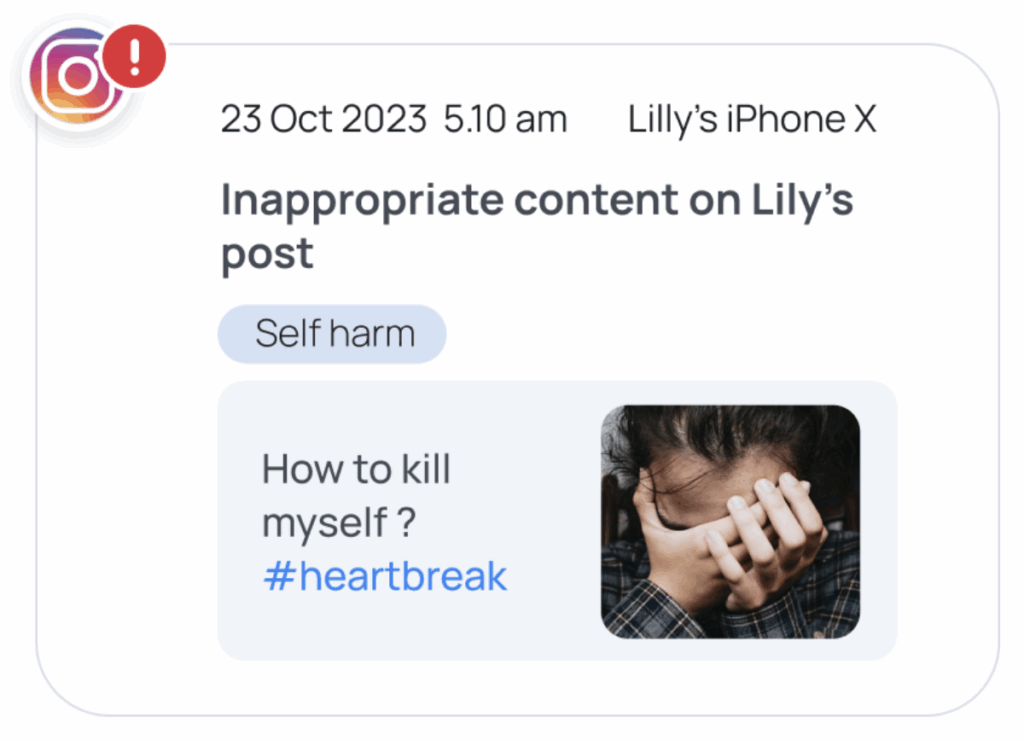
By offering a cross-platform solution (covering Android, iOS, Windows, MacOS, and Chromebooks), Mobicip ensures seamless protection across all devices.
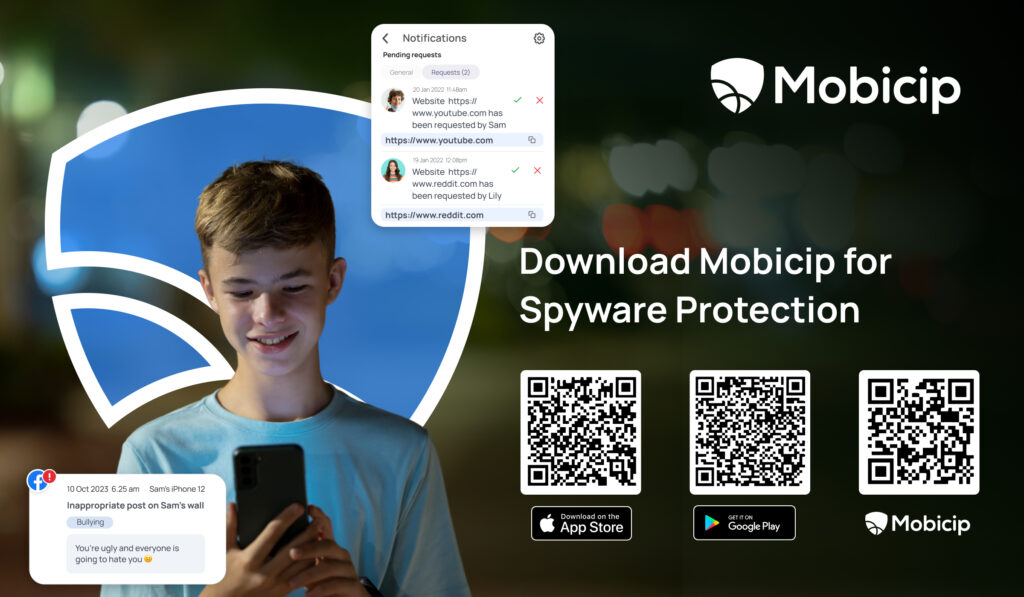
Conclusion
The rise of spyware apps disguised as productivity tools is a pressing threat in today’s connected world. These apps leverage trust and necessity to infiltrate devices and harvest sensitive information, often with devastating consequences.
However, with vigilance, education, and reliable security tools like Mobicip, users can stay a step ahead. By making smart choices and using the right technology, you can protect your privacy, your finances, and your peace of mind.
Remember: In the digital age, being productive should never mean being vulnerable.
Stay informed, stay cautious, and safeguard your digital world with Mobicip.
Leave a Reply